Even just before Christmas, we’re still hard at work helping our customers stay secure while using Storadera S3.
We recently updated our S3 service to enforce:
1. TLS 1.2 or newer
2. Only forward-secret cipher suites (ECDHE key exchange)
Why TLS 1.2 minimum
TLS 1.0 and TLS 1.1 are deprecated by RFC 8996 due to known cryptographic weaknesses (such as BEAST in TLS 1.0, legacy CBC/MAC constructions, and reliance on outdated hash algorithms).
Requiring TLS 1.2 or newer ensures access to modern cipher suites, AEAD encryption modes, and secure key exchange mechanisms.
Why these cipher suites
All selected cipher suites use ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) key exchange, which provides forward secrecy. This means that even if a server’s private key were compromised in the future, previously recorded traffic could not be decrypted.
They are combined with AEAD ciphers such as AES-GCM and ChaCha20-Poly1305, which integrate encryption and authentication in a single, secure construction. This avoids the known weaknesses of legacy CBC-mode ciphers and deprecated algorithms like 3DES.
Is this really an improvement?
Sometimes improving security isn’t about fixing an immediate problem, but about preventing future mistakes.
In practice, none of our customer traffic used TLS versions older than 1.2 or weak cipher suites. Still, this change is important to avoid outdated or legacy S3 clients being used in the future.
Statistics
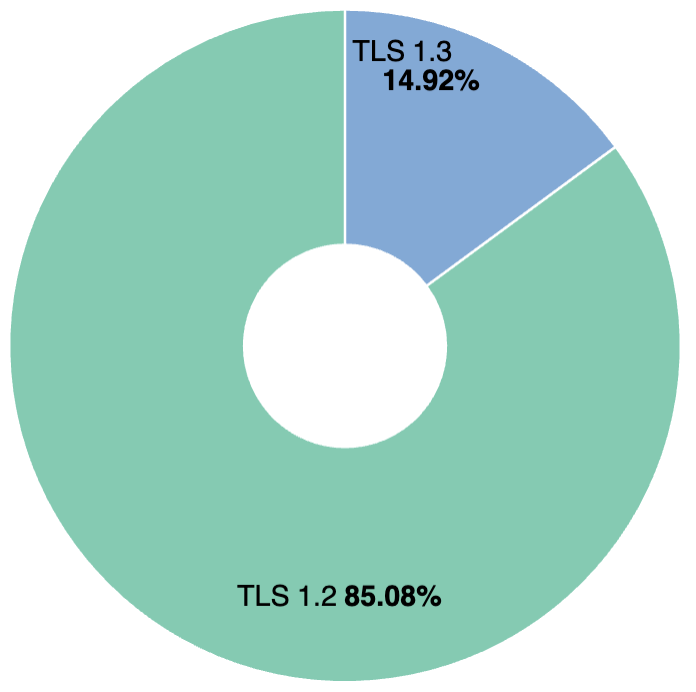
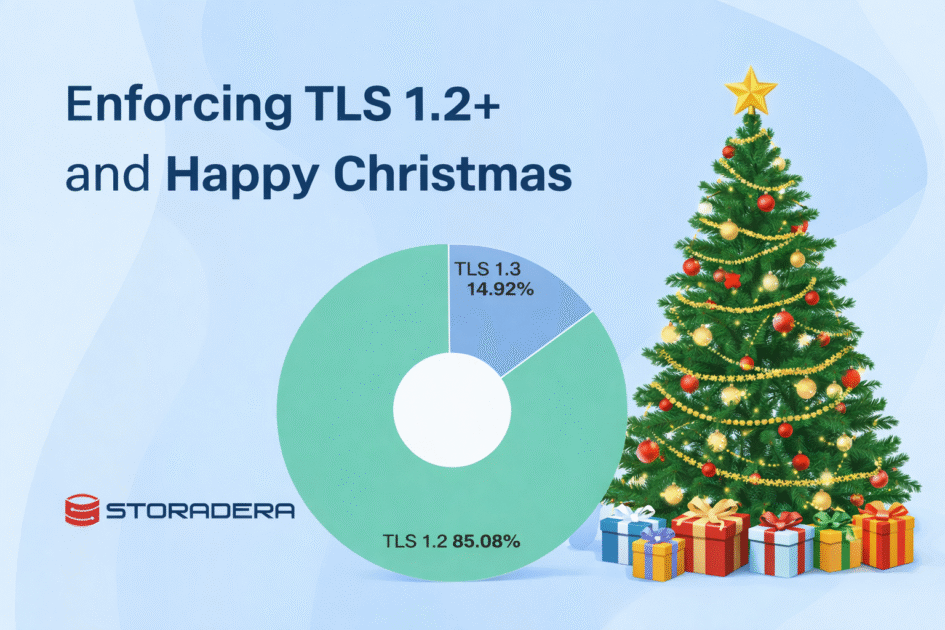
For about a week, we logged the TLS version for all S3 API requests.
I am glad to report that 100% of requests used TLS 1.2 or TLS 1.3.
| TLS 1.2 | 85.08% |
| TLS 1.3 | 14.92% |
I am slightly surprised that TLS 1.3 accounts for only about 15%, but very happy that we saw zero requests using older protocols.
Happy Christmas! 🎄